Manage Azure Web Pages From Your Desktop
You can store your web pages in Windows Azure Blob storage. After that, you can map a DNS CNAME record to your Azure Blob storage endpoint URL so your web pages become available in a web browser. It is a good way to construct a web site without the fixed hosting cost. It is also a good way to service important documents through the Azure CDN(Content Delivery Network). This tutorial describes an easy way to manage your Azure web pages directly from your Windows Explorer.
Step 1 – Map a Custom Domain to Azure Endpoint
First you need to create a new storage service in your Windows Azure account. If you have a storage service created already, you can skip this step. This is a one time setup.

After you click the Next button above, you will be asked to give your new storage account a URL in the .blob.core.windows.net sub domain. Pick a name that is good for you.

After that, your new storage account will be created. You will have your Primary Access Key assigned. Noticed that there is no custom domain mapped to the new azure endpoint yet.

Click the Manage link above, you can give a custom domain for the endpoint. Azure will ask you to validate that you are the domain admin for the custom domain. You will need to follow the instruction and setup the DNS CNAME mapping. After the CNAME records are setup, you may need to wait for a while for the DNS mapping to propagate back to the Azure or over the world. Typically it is less than one hour in the US and less than 24 hours in the world.

After all that, when you see your custom domain is in the mapped to column and the status is validated, it is all set.

Step 2 – Map a Network Drive to your Azure Account
Gladinet Cloud Desktop or Gladinet CloudAFS can help you map a network drive to your Azure Blob Storage account from Windows Explorer. You can mount your account using the Mount Cloud Storage wizard.


Step 3 – Drag and Drop Local Web Pages to Azure Blob Storage
Since the Azure Blob Storage is mapped as a network drive, you can do drag and drop your web pages from local to remote. (It is recommended that your top level folder in Azure is all lower case, longer than 3 characters and shorter than 64 characters. It is because the top level folder is an Azure container. An Azure container follows the DNS naming rules.) If your top level folder doesn’t follow the Azure container naming rules, the folder name will be decorated internally.

Step 4 – Adjust the Security Setting on Your Azure Blob Storage
By default, the documents uploaded to the Azure Blob Storage is private to the owner of the Azure account. However, in our use case here, we need to publish the web pages so the security setting needs to be public anonymous access. You can use the Gladinet Cloud Explorer to fine tune the security settings.
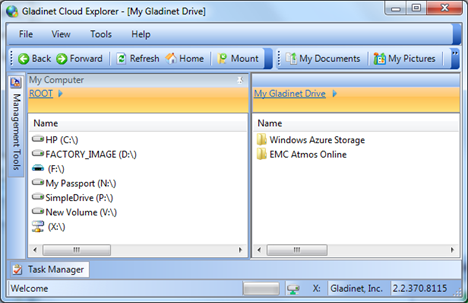
If you have documents sitting on the root folder, you will right click on the Azure Virtual Directory and set the security settings (It is the $root folder in Azure). If you have other root level folders (Azure containers), you can go through each container and set the security level to Full public read access.

The Container Security Setting is a one time setting too. You can continue to modify the documents in the container and they will inherit the security setting from the container.
Now it is all set, you can find your web pages inside the Gladinet Virtual Drive. Any modifications to the web pages will be reflected in your Azure Blob Storage. They will in turn shows up on your web pages serviced by the Azure Blob Storage through DNS CNAME mapping. Managing these web pages is as easy as modifying it in the mapped network drive.
Since Azure Blob Storage is not a web server, it doesn’t do the auto mapping such as mapping visits of / to visits of /index.htm. The best use case for this is to service some frequently downloaded files through Azure and its associated CDN service. For example, you have a PDF file that may be downloaded many times by your web site visitors and you are concerned about your bandwidth cost, you can move that PDF file to Azure Blob Storage and modify it through a mapped network drive.
Step 1 – Map a Custom Domain to Azure Endpoint
First you need to create a new storage service in your Windows Azure account. If you have a storage service created already, you can skip this step. This is a one time setup.

After you click the Next button above, you will be asked to give your new storage account a URL in the .blob.core.windows.net sub domain. Pick a name that is good for you.

After that, your new storage account will be created. You will have your Primary Access Key assigned. Noticed that there is no custom domain mapped to the new azure endpoint yet.

Click the Manage link above, you can give a custom domain for the endpoint. Azure will ask you to validate that you are the domain admin for the custom domain. You will need to follow the instruction and setup the DNS CNAME mapping. After the CNAME records are setup, you may need to wait for a while for the DNS mapping to propagate back to the Azure or over the world. Typically it is less than one hour in the US and less than 24 hours in the world.

After all that, when you see your custom domain is in the mapped to column and the status is validated, it is all set.

Step 2 – Map a Network Drive to your Azure Account
Gladinet Cloud Desktop or Gladinet CloudAFS can help you map a network drive to your Azure Blob Storage account from Windows Explorer. You can mount your account using the Mount Cloud Storage wizard.


Step 3 – Drag and Drop Local Web Pages to Azure Blob Storage
Since the Azure Blob Storage is mapped as a network drive, you can do drag and drop your web pages from local to remote. (It is recommended that your top level folder in Azure is all lower case, longer than 3 characters and shorter than 64 characters. It is because the top level folder is an Azure container. An Azure container follows the DNS naming rules.) If your top level folder doesn’t follow the Azure container naming rules, the folder name will be decorated internally.

Step 4 – Adjust the Security Setting on Your Azure Blob Storage
By default, the documents uploaded to the Azure Blob Storage is private to the owner of the Azure account. However, in our use case here, we need to publish the web pages so the security setting needs to be public anonymous access. You can use the Gladinet Cloud Explorer to fine tune the security settings.

If you have documents sitting on the root folder, you will right click on the Azure Virtual Directory and set the security settings (It is the $root folder in Azure). If you have other root level folders (Azure containers), you can go through each container and set the security level to Full public read access.

The Container Security Setting is a one time setting too. You can continue to modify the documents in the container and they will inherit the security setting from the container.
Now it is all set, you can find your web pages inside the Gladinet Virtual Drive. Any modifications to the web pages will be reflected in your Azure Blob Storage. They will in turn shows up on your web pages serviced by the Azure Blob Storage through DNS CNAME mapping. Managing these web pages is as easy as modifying it in the mapped network drive.
Since Azure Blob Storage is not a web server, it doesn’t do the auto mapping such as mapping visits of / to visits of /index.htm. The best use case for this is to service some frequently downloaded files through Azure and its associated CDN service. For example, you have a PDF file that may be downloaded many times by your web site visitors and you are concerned about your bandwidth cost, you can move that PDF file to Azure Blob Storage and modify it through a mapped network drive.


Comments